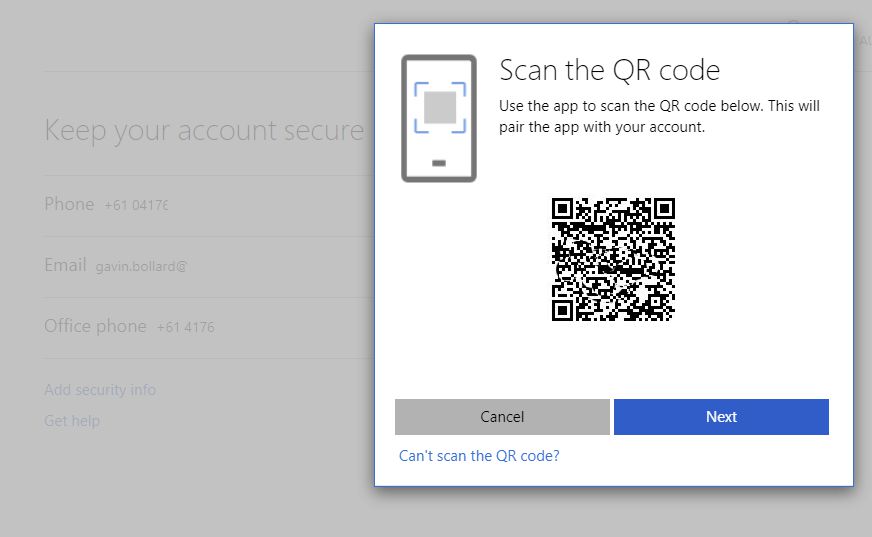
Remote Connect: Access Your PC From Anywhere - Aka.ms/remoteconnect
Accessing Remote Resources: Understanding a Critical Link
This shortened URL represents a frequently used method for connecting to remote resources, typically those hosted within a corporate network or a similar secure environment. It often facilitates remote desktop access or other remote functionalities. For example, this link might direct users to software that allows them to control a desktop located in a different location, similar to virtual desktop access.
The importance of this type of connection lies in its ability to enable workers and users to engage with systems and data from various geographical locations. This flexibility fosters increased productivity and accessibility. The use of such a connection method has grown significantly alongside the rise of remote work and cloud-based services. Its role in maintaining business continuity and enabling remote collaborations is evident. Historically, this process was often more cumbersome; the availability of abbreviated URLs dramatically improved ease of use and efficiency.
Read also:Hd Hub4ucom Free Hd Movies Tv Shows
Further exploration into this connection method will illuminate the technical protocols involved, various security measures, and optimal usage scenarios. This analysis will aid in maximizing the benefits and minimizing potential risks associated with remote access to this specific link.
aka.ms/remoteconnect
Understanding the intricacies of "aka.ms/remoteconnect" reveals crucial aspects of modern remote access. This URL shortener facilitates various connectivity needs, highlighting the significance of efficient and secure remote communication channels.
- Remote Access
- Virtual Desktop
- Corporate Network
- Security Protocols
- Cloud Connectivity
- Remote Collaboration
- User Experience
The listed aspects interconnect. "Remote Access" is facilitated through "Virtual Desktop" and "Corporate Network" configurations, secured by specific "Security Protocols." "Cloud Connectivity" underscores the modern nature of these systems, enabling "Remote Collaboration." A positive "User Experience" ultimately hinges on efficient "Remote Access" protocols. For instance, a well-designed "Virtual Desktop" experience optimized for various devices translates to enhanced user productivity in remote settings, exemplifying how these elements contribute to a comprehensive user experience.
1. Remote Access
The connection between remote access and "aka.ms/remoteconnect" is fundamental. "Remote Access" describes the ability to connect to and utilize resources located in a different physical location. "aka.ms/remoteconnect" serves as a specific, often shortened, method for initiating such a connection. This abbreviated URL likely directs users to tools or interfaces enabling remote control of computers, servers, or applications within a network. Essentially, "aka.ms/remoteconnect" acts as a gateway for remote access, providing a convenient pathway to connect to systems, files, and data housed elsewhere.
Real-world examples abound. A company employee working from home might utilize "aka.ms/remoteconnect" to access their office computer and complete work tasks remotely. Similarly, a technician might connect to a server in a different location to troubleshoot an issue. The critical element in both scenarios is the smooth functioning of remote access technology enabled by a designated URL, in this case "aka.ms/remoteconnect." This understanding is vital for implementing and utilizing remote work models, maintaining operational continuity, and troubleshooting technical problems across geographically dispersed systems.
In summary, "aka.ms/remoteconnect" is a significant component of a broader remote access strategy. Understanding this link underscores the importance of reliable and secure remote connectivity in today's work environment and beyond. This connection facilitates access to critical resources regardless of physical location, directly impacting productivity, efficiency, and overall operational effectiveness. Furthermore, the ability to access and manage systems remotely becomes paramount in maintaining business continuity in case of disruptions or emergencies.
Read also:Hugh Jackman Iconic Performances Beyond
2. Virtual Desktop
A virtual desktop, often accessed through a dedicated URL like "aka.ms/remoteconnect," represents a crucial component of modern remote access strategies. A virtual desktop allows users to interact with a computer's graphical user interface (GUI) and applications as if they were physically present at the machine. This remote interaction is crucial for enabling work from various locations and supporting flexible work models. The underlying technology typically involves connecting a user's device to a remote server hosting the virtual desktop environment. This server processes applications and displays, presenting a virtual representation of the desktop for the user to manipulate. The URL facilitates this connection by directing users to the specific access portal or software necessary.
The practical significance of this connection is profound. Consider a software engineer working from home. Through a secure virtual desktop environment accessed via "aka.ms/remoteconnect," they can access company servers, applications, and files located at the office. This allows seamless collaboration and work continuity. Similarly, IT support personnel can access and manage remote systems efficiently for troubleshooting and maintenance. The availability of virtual desktops, accessible through designated URLs, facilitates operational efficiency and responsiveness in dynamic work environments. By providing access to a complete desktop environment remotely, a well-implemented virtual desktop system ensures consistent functionality, regardless of physical location.
In conclusion, the connection between virtual desktops and a dedicated URL like "aka.ms/remoteconnect" is pivotal for remote work and IT management. This connection facilitates seamless access to remote resources and promotes flexibility and operational continuity. The successful implementation of virtual desktops hinges on secure and reliable remote access mechanisms. Understanding this connection, therefore, underpins the advantages and practicality of modern remote access solutions. The importance of secure connectivity protocols and proper configuration is paramount in ensuring a secure and reliable virtual desktop experience.
3. Corporate Network
A corporate network underpins the functionality of remote access facilitated by a URL like "aka.ms/remoteconnect." This network serves as the central repository for resources, applications, and data accessed remotely. Understanding the network's structure and security protocols is crucial for evaluating the effectiveness of remote connections.
- Resource Availability
The corporate network houses critical resources, including applications, data, and servers. Remote access, mediated by "aka.ms/remoteconnect," relies on these resources being accessible across geographical boundaries. Effective remote access depends on network infrastructure ensuring these resources are available for use outside the immediate physical location. Examples include financial databases accessible for remote reporting, or project management software available for collaboration from different office locations.
- Security Infrastructure
The corporate network implements security protocols to protect sensitive data and resources. These security measures are crucial for remote access. A secure network architecture, coupled with the appropriate authentication methods, is necessary for authorized remote access, mitigating risks associated with potential security breaches. This frequently includes firewalls, intrusion detection systems, and authentication protocols, which are essential for secure remote connectivity through links like "aka.ms/remoteconnect."
- Network Architecture and Protocols
The structure and protocols of the corporate network directly impact remote access performance. The type of network topology, whether a simple LAN, a complex WAN, or a hybrid configuration, influences data transfer speed and reliability. This directly affects remote connection efficiency. Different network protocols, including TCP/IP and VPNs, play a key role in delivering secure and reliable remote access. These network features are crucial for supporting remote users' ability to access the corporation's network effectively through "aka.ms/remoteconnect."
- Access Control Mechanisms
A corporate network utilizes access control mechanisms to regulate user access to specific resources. These mechanisms underpin the authorized use of resources available through a link like "aka.ms/remoteconnect." Appropriate permissions and security policies are critical, controlling which users can access which data and applications remotely. The network's access control features form a critical component in ensuring the secure and controlled flow of information and data.
In conclusion, the corporate network forms the foundation for remote access solutions. Its security, architecture, and resource availability are directly related to the effectiveness of connections mediated by a URL such as "aka.ms/remoteconnect." A robust corporate network allows secure and seamless access to critical resources for employees and authorized users regardless of their physical location. The network's architecture and implemented security measures directly affect the efficiency and reliability of remote access services, thereby enhancing overall productivity and security.
4. Security Protocols
Security protocols are intrinsically linked to a URL like "aka.ms/remoteconnect." This connection hinges on the secure transmission of data and authentication of users accessing remote resources. Without robust security protocols, the risk of unauthorized access, data breaches, and system compromise is significantly heightened. The effectiveness and trustworthiness of "aka.ms/remoteconnect" directly correlate with the strength and implementation of these security protocols.
Practical examples illustrate this relationship. Consider a financial institution utilizing "aka.ms/remoteconnect" to allow employees access to sensitive data. Strong encryption protocols, such as Transport Layer Security (TLS), are paramount to safeguarding financial information transmitted during login or data retrieval. Multi-factor authentication (MFA) further reinforces security by demanding verification from multiple sources, effectively adding another layer of protection against unauthorized access attempts. Similarly, in a healthcare setting, secure access to patient records through a remote connection, facilitated by "aka.ms/remoteconnect", necessitates the implementation of strict security protocols to prevent unauthorized access and maintain data confidentiality, often incorporating measures such as role-based access control (RBAC).
Understanding the interplay between security protocols and a remote access URL like "aka.ms/remoteconnect" is critical for maintaining data integrity and system security. Robust authentication and encryption mechanisms are essential components for secure remote access, preventing unauthorized access and minimizing the potential for data breaches. The appropriate implementation of security protocols within the context of remote access is paramount for ensuring the safety and reliability of sensitive data and preventing potential misuse. Furthermore, adhering to industry best practices for security protocols, and keeping those protocols up-to-date with emerging threats, is crucial for the ongoing security and reliability of remote access solutions.
5. Cloud Connectivity
Cloud connectivity is a crucial component of a URL like "aka.ms/remoteconnect." The connection facilitates remote access to resources hosted in cloud environments. Data centers, applications, and virtual desktops hosted in cloud platforms are typically accessed through such a link. This access relies heavily on established cloud infrastructure providing the underlying communication channels. Therefore, the quality and reliability of cloud connectivity directly impact the efficacy of connections initiated via "aka.ms/remoteconnect." Examples include accessing cloud-based collaboration tools or utilizing cloud storage remotely.
Cloud connectivity's importance extends beyond simple access. Efficient access to cloud-based resources is vital for many applications. Consider a remote team working on a shared document repository residing in a cloud service. A dedicated connection initiated through "aka.ms/remoteconnect" depends on reliable cloud infrastructure; poor connectivity can lead to slow response times, data loss, or even service interruption, directly affecting productivity. Likewise, in enterprise environments where virtual desktops are hosted in the cloud, cloud connectivity is fundamental for smooth operation and user experience. Any disruption to this connectivity translates to service impairment. Thus, understanding the relationship between cloud connectivity and remote access facilitated by a URL like "aka.ms/remoteconnect" is essential for effective remote operations.
In summary, cloud connectivity is a foundational aspect for a URL like "aka.ms/remoteconnect." Robust cloud infrastructure ensures reliable and efficient access to resources. Weaknesses in cloud connectivity directly impact the experience and functionality of a remote connection. This connection becomes even more critical for organizations relying heavily on cloud services for various operational needs. Understanding this dependency underscores the importance of robust cloud infrastructure for maintaining secure, efficient, and high-performance remote access solutions.
6. Remote Collaboration
The connection between remote collaboration and a URL like "aka.ms/remoteconnect" is fundamental. Remote collaboration, the ability for individuals to work together on projects or tasks despite physical separation, directly benefits from reliable remote access mechanisms. A URL like "aka.ms/remoteconnect" often serves as the gateway for these collaborative efforts. Through this link, participants gain access to shared resources, applications, and data, facilitating joint problem-solving, information exchange, and project development. The efficiency of remote collaboration, therefore, hinges on the stability and functionality of the underlying remote access technology.
Real-world examples highlight this interplay. Consider a team of software developers working on a cross-country project. A crucial component of their collaborative process might involve access to a shared code repository, facilitated by remote access tools initiated through a URL like "aka.ms/remoteconnect." This enables simultaneous code editing, version control, and communication, enhancing project velocity and quality. Similarly, in a marketing campaign, teams dispersed across different locations can collaborate effectively on design concepts, content creation, and data analysis if the necessary resources are accessible remotely via a URL like "aka.ms/remoteconnect," enabling shared workspaces and communication platforms.
Understanding the connection between remote collaboration and a URL like "aka.ms/remoteconnect" reveals the importance of seamless remote access in modern workplaces. It underscores the need for robust infrastructure, dependable security protocols, and user-friendly interfaces to facilitate efficient teamwork. A breakdown in the remote connection or access security negatively impacts the collaborative process. This connection underscores the crucial role technology plays in enabling effective global teamwork and facilitating project completion across geographical boundaries. This insight is essential for organizations striving to optimize their remote work strategies and maximize the benefits of dispersed teams.
7. User Experience
User experience (UX) is intrinsically linked to a URL like "aka.ms/remoteconnect." A positive UX surrounding this connection significantly impacts the effectiveness and adoption of remote access solutions. A poorly designed or implemented user experience can hinder productivity, increase frustration, and ultimately lead to user dissatisfaction and abandonment of the remote access platform. Conversely, a seamless and intuitive UX enhances user satisfaction and encourages consistent use of the remote access service, whether it's for accessing corporate resources, collaborating on projects, or managing remote systems.
Several factors contribute to a positive UX related to "aka.ms/remoteconnect." Intuitive navigation and clear instructions are paramount. The simplicity of the login process, ease of accessing desired resources, and the overall responsiveness of the system directly influence the user experience. Visual clarity and a well-structured interface minimize user confusion and maximize efficiency. The ability for users to quickly and effortlessly accomplish their objectives via "aka.ms/remoteconnect" directly contributes to a positive overall experience. Furthermore, proactive error handling and helpful support options contribute to a smoother experience during any technical difficulties. Consider a medical professional needing to access patient records remotely. A user-friendly interface and swift access to relevant information foster efficiency and improve the quality of care. This, in turn, positively impacts the user experience.
In conclusion, a well-considered user experience plays a pivotal role in the success of remote access solutions facilitated by URLs like "aka.ms/remoteconnect." A positive UX contributes to increased user satisfaction, enhanced productivity, and greater adoption of remote access platforms. Understanding and prioritizing UX elements are essential for the development of robust and reliable remote solutions. Ignoring this crucial aspect can lead to user frustration, decreased efficiency, and reduced overall system effectiveness. This principle is applicable across various sectors and underscores the critical need for UX design considerations in all remote access applications.
Frequently Asked Questions about "aka.ms/remoteconnect"
This section addresses common inquiries regarding the URL "aka.ms/remoteconnect," focusing on its functionalities, security, and practical applications. These answers provide clarity and guidance for users seeking to understand and utilize this remote access tool effectively.
Question 1: What is the purpose of "aka.ms/remoteconnect"?
The URL "aka.ms/remoteconnect" typically serves as a gateway for remote access to resources, often within a corporate or institutional network. This might include accessing virtual desktops, specific applications, or shared data. The precise function depends on the system configuration.
Question 2: Is "aka.ms/remoteconnect" secure?
Security is paramount. The security of "aka.ms/remoteconnect" depends heavily on the implemented security protocols within the target network. Robust security measures, such as encryption and multi-factor authentication, are crucial for protecting data and preventing unauthorized access.
Question 3: How do I use "aka.ms/remoteconnect"?
Instructions for utilizing "aka.ms/remoteconnect" vary based on the specific system and organization. Consult the organization's documentation or IT support for detailed instructions tailored to their network.
Question 4: What happens if my connection fails?
Connection failures can stem from various factors, including network issues, authentication failures, or software glitches. Troubleshooting guides from the organization managing the resource or IT support should assist in resolving such issues. Contacting IT support directly is often recommended.
Question 5: What are the limitations of "aka.ms/remoteconnect"?
Limitations vary depending on the network infrastructure and the specific application or service accessed. Potential limitations may include access restrictions based on user roles, network bandwidth constraints, or specific software compatibility requirements.
In summary, "aka.ms/remoteconnect" facilitates remote access to network resources, but its successful use relies on secure infrastructure, appropriate user authentication, and adherence to organizational guidelines. Users should seek clarification regarding security protocols and the applicable limitations associated with the particular system or service. Understanding these details ensures effective and secure utilization.
The subsequent section will explore the technical aspects of remote access methodologies further.
Conclusion
The exploration of "aka.ms/remoteconnect" reveals a critical aspect of contemporary remote access. This shortened URL, or similar constructs, represents a vital gateway for connecting to resources located outside of immediate physical proximity. Key factors contributing to its functionality include robust security protocols, reliable cloud connectivity, and well-structured corporate networks. The efficiency of remote collaboration, the effectiveness of virtual desktop environments, and the maintenance of business continuity all depend upon the consistent and secure operation of such access mechanisms. Moreover, user experience significantly impacts the overall effectiveness of the remote access system facilitated by "aka.ms/remoteconnect" or similar links. The need for seamless and intuitive interfaces, and clear protocols, is paramount.
Moving forward, the strategic importance of secure and reliable remote access will continue to grow. Organizations must prioritize the development and maintenance of robust infrastructure to support remote operations. Addressing security concerns, optimizing user experience, and ensuring seamless integration with cloud technologies are vital steps in the ongoing evolution of remote access methods. Understanding the intricacies of tools like "aka.ms/remoteconnect" and their supporting technologies provides a critical framework for organizations to adapt to the dynamic demands of modern work environments.