Best SSH RemoteIoT: Unlocking Secure Access For Your IoT Devices
Let's face it, folks—IoT devices are everywhere these days. But how do you manage them securely from afar? Enter the world of SSH RemoteIoT. If you're scratching your head wondering what that means, don't worry—you're not alone. In this article, we’re diving deep into the best SSH RemoteIoT solutions to help you keep your devices safe and accessible.
Imagine this: you're sitting at home, chilling with your favorite beverage, and suddenly you need to check on your smart thermostat miles away. How do you do that without exposing yourself to cyber threats? That’s where SSH RemoteIoT comes in. It’s like the Swiss Army knife of secure remote access for all your IoT toys.
Now, before we get into the nitty-gritty, let me tell you something. This isn’t just another tech article. We’re going to break it down in a way that even your grandma could understand—or at least pretend to. So, buckle up, because we’re about to take a ride through the world of SSH RemoteIoT, and by the end of it, you’ll be a pro.
Read also:Danielle Cohn Porn The Truth Behind The Viral Sensation
What Exactly Is SSH RemoteIoT?
SSH RemoteIoT is basically the marriage of two awesome things: SSH (Secure Shell) and IoT (Internet of Things). SSH is like a digital bodyguard that protects your data when you're accessing devices remotely. IoT, on the other hand, is all about connecting everyday devices to the internet so they can talk to each other. Put them together, and you’ve got a powerful combo that lets you control your smart devices from anywhere, safely and securely.
Why You Need SSH for IoT
Here's the deal: IoT devices are super convenient, but they’re also a goldmine for hackers. Without proper security, your smart fridge could end up being the weakest link in your digital fortress. That’s where SSH comes in. It encrypts your data, making it nearly impossible for bad actors to snoop around or take control of your devices.
- SSH provides encryption for data in transit.
- It authenticates users and devices, ensuring only authorized parties can access your IoT setup.
- SSH helps protect against common cyber threats like man-in-the-middle attacks.
Top Benefits of Using SSH RemoteIoT
Alright, let’s talk about why SSH RemoteIoT is the real MVP in the world of IoT security. Here are some of the top benefits that make it a must-have for anyone serious about protecting their connected devices.
Enhanced Security
First and foremost, SSH RemoteIoT offers rock-solid security. It uses advanced encryption protocols to safeguard your data, making it nearly impossible for hackers to intercept or tamper with your communications. Think of it like a digital fortress surrounding your IoT ecosystem.
Seamless Remote Access
With SSH RemoteIoT, you can access your devices from anywhere in the world. Whether you're on vacation or working from a coffee shop, you can keep an eye on your smart home setup without lifting a finger. It’s like having a remote control for your entire digital life.
Cost-Effective Solution
Let’s be real—security solutions can get pricey. But SSH RemoteIoT is a cost-effective option that delivers top-notch protection without breaking the bank. You don’t need to invest in expensive hardware or software to get started. All you need is a bit of know-how and the right tools.
Read also:Empowering Digital Awareness A Guide To Responsible Internet Use
The Best SSH RemoteIoT Tools
Now that you know why SSH RemoteIoT is a game-changer, let’s talk about some of the best tools you can use to implement it. These aren’t just any tools—they’re the cream of the crop, trusted by professionals and hobbyists alike.
1. OpenSSH
OpenSSH is like the OG of SSH tools. It’s open-source, which means it’s free to use and highly customizable. With OpenSSH, you can set up secure connections between your devices in no time. It’s also super reliable, so you can trust it to keep your IoT setup safe and sound.
2. Bitvise SSH Client
If you’re looking for a user-friendly SSH client, Bitvise is the way to go. It’s packed with features like file transfer, terminal emulation, and tunneling, making it a one-stop-shop for all your SSH needs. Plus, it’s available for both Windows and Linux, so you can use it on pretty much any device.
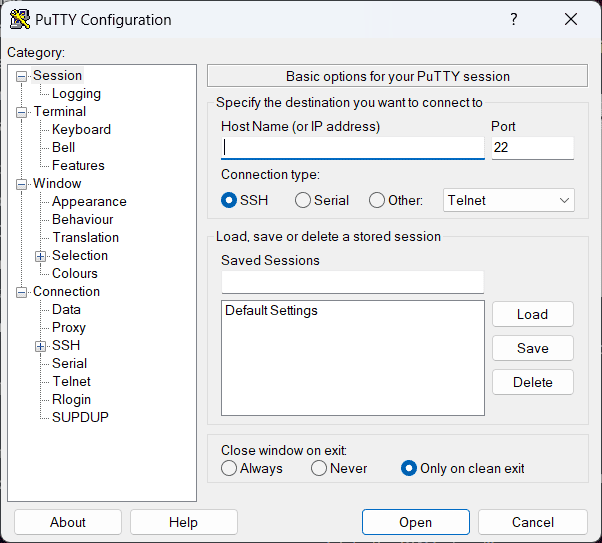
3. PuTTY
PuTTY is another popular choice for SSH RemoteIoT enthusiasts. It’s lightweight, easy to use, and supports a variety of protocols. Whether you’re a tech wizard or a complete newbie, PuTTY has got your back. And the best part? It’s completely free!
Setting Up SSH RemoteIoT: A Step-by-Step Guide
Now, let’s get our hands dirty and talk about how to set up SSH RemoteIoT. Don’t worry if you’re not a tech guru—we’ve got you covered with this simple step-by-step guide.
Step 1: Install an SSH Client
The first thing you need to do is install an SSH client on your computer. If you’re using a Mac or Linux machine, you’re in luck—OpenSSH is already installed. For Windows users, you’ll need to download a client like PuTTY or Bitvise.
Step 2: Enable SSH on Your IoT Device
Next, you’ll need to enable SSH on your IoT device. Most modern IoT devices come with SSH support out of the box, but you may need to tweak some settings to get it up and running. Check the device’s documentation for specific instructions.
Step 3: Connect to Your Device
Once everything is set up, it’s time to connect to your device. Open your SSH client, enter your device’s IP address, and hit connect. If everything goes smoothly, you should be able to access your device from anywhere in the world.
Common Challenges and How to Overcome Them
Let’s be honest—setting up SSH RemoteIoT isn’t always a walk in the park. There are a few common challenges you might run into along the way. But don’t worry—we’ve got some tips to help you overcome them.
Firewall Issues
One of the most common problems people face is firewall restrictions. If you can’t connect to your device, it might be because your firewall is blocking the connection. Check your firewall settings and make sure SSH traffic is allowed through.
Authentication Problems
Another issue you might encounter is authentication problems. If you’re having trouble logging in, double-check your username and password. You might also want to consider using SSH keys for added security and convenience.
Best Practices for SSH RemoteIoT
Now that you know how to set up SSH RemoteIoT, let’s talk about some best practices to keep your setup running smoothly and securely.
- Use strong passwords or SSH keys for authentication.
- Regularly update your devices and SSH software to patch security vulnerabilities.
- Limit access to only trusted users and devices.
- Monitor your logs for suspicious activity.
Real-World Applications of SSH RemoteIoT
SSH RemoteIoT isn’t just for tech enthusiasts—it has a wide range of real-world applications. From smart homes to industrial automation, here are some examples of how people are using SSH RemoteIoT to improve their lives.
Smart Home Management
With SSH RemoteIoT, you can manage your smart home devices from anywhere. Whether you’re adjusting the thermostat or checking on your security cameras, SSH ensures your data stays safe and secure.
Industrial Automation
In the world of industrial automation, SSH RemoteIoT is a lifesaver. It allows engineers to remotely monitor and control machinery, reducing downtime and improving efficiency. Plus, it helps protect sensitive industrial data from cyber threats.
Data and Statistics: The Power of SSH RemoteIoT
Let’s talk numbers for a moment. According to a recent report by Gartner, the number of connected IoT devices is expected to reach 25 billion by 2025. That’s a lot of devices, and it highlights the growing need for secure remote access solutions like SSH RemoteIoT.
Another study by Cisco found that 60% of companies have experienced a data breach due to unsecured IoT devices. This underscores the importance of implementing robust security measures, like SSH, to protect your IoT ecosystem.
Conclusion: Why SSH RemoteIoT Matters
So, there you have it—everything you need to know about SSH RemoteIoT. From enhancing security to enabling seamless remote access, SSH RemoteIoT is a game-changer in the world of IoT. By following the tips and best practices outlined in this article, you can keep your devices safe and secure while enjoying the convenience of remote access.
Now it’s your turn. Have you tried SSH RemoteIoT? What are your favorite tools and techniques? Leave a comment below and let’s start a conversation. And don’t forget to share this article with your friends and colleagues—spread the word about the power of SSH RemoteIoT!
Table of Contents
- What Exactly Is SSH RemoteIoT?
- Why You Need SSH for IoT
- Top Benefits of Using SSH RemoteIoT
- The Best SSH RemoteIoT Tools
- Setting Up SSH RemoteIoT: A Step-by-Step Guide
- Common Challenges and How to Overcome Them
- Best Practices for SSH RemoteIoT
- Real-World Applications of SSH RemoteIoT
- Data and Statistics: The Power of SSH RemoteIoT
- Conclusion: Why SSH RemoteIoT Matters